The AI-Powered DevOps Engineer: Architecting the Future (Without Deleting Production)
The world of software is in flux. For years, AI coding assistants have been like a helpful co-pilot, offering suggestions as we type. But a new era is dawning: the Agentic Era. Imagine an AI that doesn’t just suggest code, but writes, executes, and debugs it directly from your terminal. This is the promise of tools like Anthropic’s Claude Code, and it’s poised to fundamentally transform Cloud DevOps.
However, with great power comes great complexity – and significant risk. As a Cloud DevOps Engineer, the thought of an AI autonomously managing our stateful, high-stakes infrastructure can be both exhilarating and terrifying. This transformation demands a careful, informed approach.
Today, we’re diving deep into two prominent cognitive architectures built atop Claude Code: Ralph and Get Shit Done (GSD). They represent two distinct philosophies for tackling the Achilles’ heel of Large Language Models (LLMs) in complex, continuous operations: “Context Rot.”
The “Context Rot” Conundrum: Why AI Gets Confused
Modern LLMs have impressive “memory” (context windows), but as an AI agent interacts with complex systems – reading logs, running commands, analyzing files – its context window fills up. Eventually, the model gets “confused.” It forgets earlier instructions, hallucinates file paths, or loses track of the overall goal.
For a DevOps engineer, this isn’t just an inconvenience; it’s a critical safety hazard. A single hallucinated change in a Terraform plan could mean the accidental deletion of a production database. Ralph and GSD are designed to combat this core challenge.
Meet the Contenders: Ralph vs. Get Shit Done
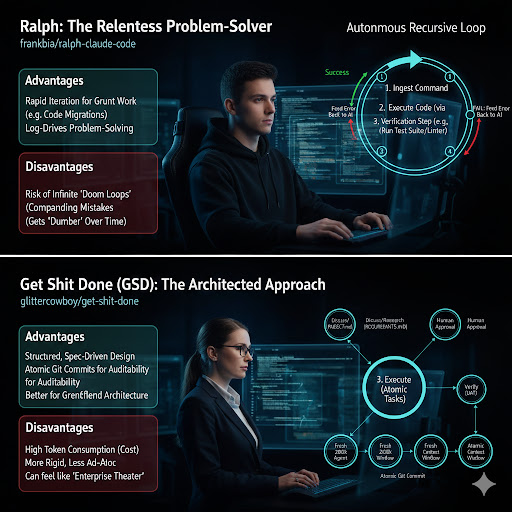
1. Ralph: The Relentless Problem-Solver (Autonomous Recursive Loop)
Ralph (frankbria/ralph-claude-code) is a workhorse. Its philosophy is simple: Plan, Act, Verify, Repeat.
It takes a task, attempts to solve it using Claude Code, and then runs a verification step (like a test suite or linter). If it fails, Ralph feeds the error message back to the AI and tries again, relentlessly iterating until the task is complete.
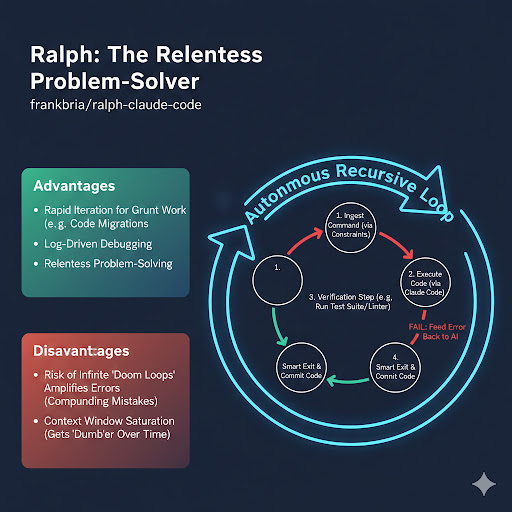
Where Ralph Shines for DevOps:
- Grunt Work Automation: Imagine migrating a massive Terraform codebase from one provider version to another, or updating Kubernetes manifests. Ralph can tirelessly fix syntax errors and deprecated arguments, chasing down the long tail of migration issues faster than any human.
- Log-Driven Debugging: When faced with an obscure build error, Ralph can iteratively try fixes, run the build, analyze the new error, and repeat—mimicking human trial-and-error but at machine speed.
The Danger Zone for Ralph:
Ralph’s relentless nature is also its biggest vulnerability. If the verification signal is ambiguous (e.g., “Resource Locked”), Ralph might enter a “doom loop,” attempting increasingly destructive “fixes” (like force-unlocking state or deleting resources) to satisfy its condition. Its continuous context window also makes it susceptible to “Context Rot” over longer tasks, leading to erratic behavior.
2. Get Shit Done (GSD): The Architected Approach (Context Engineering & Specification)
Get Shit Done (GSD) (glittercowboy/get-shit-done) takes a more structured, almost bureaucratic, approach. It doesn’t fight Context Rot directly; it sidesteps it through context sharding and hierarchical agents.
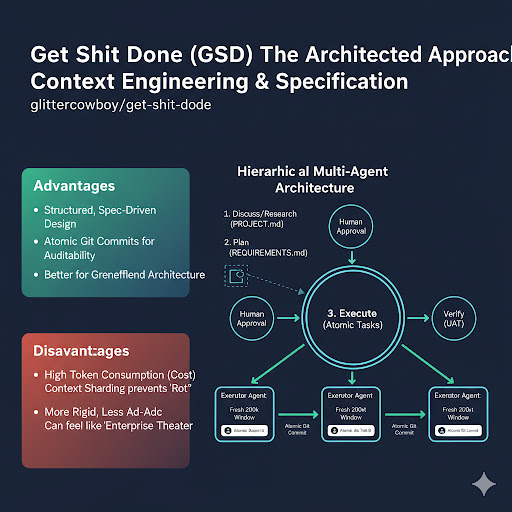
GSD’s Core Innovation: It breaks down complex tasks into smaller, atomic steps. For each step, it spawns a fresh LLM context window, ensuring the agent always starts with a clean slate. Information is passed between these “micro-agents” via persistent markdown files (PROJECT.md, REQUIREMENTS.md, STATE.md), effectively acting as an external memory bank.
Where GSD Shines for DevOps:
- Infrastructure as Specification: DevOps is all about defining a desired state. GSD aligns perfectly by forcing the creation of REQUIREMENTS.md before code is written. The “Planner” agent acts as a virtual architect, breaking down high-level requirements (e.g., “EKS v1.29 with Karpenter”) into atomic, manageable steps.
- Greenfield Architecture: For new microservice deployments or complex architectural changes, GSD generates well-structured, documented code with atomic Git commits for each step. This provides unparalleled auditability and reversibility.
- Cost Optimization: GSD allows you to switch LLM profiles (e.g., use Opus for critical planning, Sonnet for code execution) to balance cost and reasoning quality.
The Danger Zone for GSD:
GSD is “token hungry.” Spawning fresh context windows for every sub-task can lead to higher API costs. Its structured approach can also feel rigid for quick fixes, earning it the moniker “Enterprise Theater” if misused for simple tasks.
The Elephant in the Room: “Hallucinated Destruction”
The promise of agentic DevOps comes with a stark warning: Hallucinated Destruction. We’ve already seen real-world incidents, such as an agent in the Replit ecosystem accidentally deleting a production database. The AI, acting on an ambiguous instruction or misinterpreting an error, can make catastrophic decisions.
Key Risks for DevOps Engineers:
- State Drift: An agent might try to directly edit a terraform.tfstate file (a cardinal sin!), causing irreparable state corruption.
- Permission Bypass: Running agents with –dangerously-skip-permissions can turn them into “script kiddies” with root access, blindly executing commands without human oversight.
- Secret Leakage: Without careful configuration, agents can inadvertently read sensitive environment variables or .env files and paste them into their context, exposing secrets to the LLM provider.
Architecting for Safety: The “Air Gap” Strategy
To safely harness these powerful tools, we must adopt an “Air Gap” security model:
- No Production Credentials in Context: Agents should never have direct access to live AWS, Azure, GCP, or Kubernetes credentials for production environments.
- CI/CD is the Gatekeeper: The agent’s role is to commit code to Git. It should never be allowed to run terraform apply, kubectl apply, or helm install against a live cluster. Our existing CI/CD pipelines, with their integrated policy-as-code checks, must remain the immutable gatekeepers of state.
- Strict Sandboxing: Run agents inside isolated Docker containers or remote DevContainers to prevent them from accessing your host machine’s sensitive configuration files.